The importance of a secure website platform can sometimes be overlooked. With dozens of options available, most website owners pay little attention to the "small print" and look for the most user-friendly Content Management System (CMS), typically bypassing important technical specifics, including security issues. The most alluring of the ease-of-use CMS and site-builder platforms is WordPress. WebSight Design discourages clients from using WordPress as their main site host for various reasons, however believes WordPress to be a practical platform for blog use.
At WSD, we have our own CMS, custom built for each client. We then include WordPress, strictly for blogging. What we also include for our clients who use WordPress for blog purposes is the assurance that their blog will be frequently audited. WSD actively monitors the latest hacking and security breaches. We proactively protect our clients' accounts with the latest plugins and code-level adjustments.
WordPress is exceedingly susceptible to malicious attacks, specifically through the comments section on their sites. With the availability for anyone to comment on a post, it's essentially an open invitation for a Distributed Denial-of-Service (DDoS) attack. DDoS attacks are generally an attempt to make a site unavailable to visitors and/or users by flooding it with traffic.
In a recent case, the attack was generated through Pingback, a default setting in WordPress that allows blog owners to be notified when their blog is mentioned on another blog. For Pingbacks to work successfully, both blogs have to have Pingbacks enabled, which is why this is a default "enabled" setting in WordPress. Over the course of a few hours, the targeted site was attacked by hundreds of thousands different legitimate WordPress sites, which had been instructed by one hacker to ping this specific site. The hacker used XML-RPC "“ a "remote procedure call" command through the use of Pingbacks to herd the hundreds of thousands of WordPress sites into an involuntary botnet. The attacker successfully shut down the targeted site, all by ways that were completely available to him because of lack of awareness by site owners of default settings in WordPress.
For you visual learners:
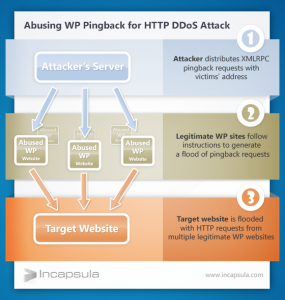
You can be certain that a site hosted by WebSight Design will not be susceptible to these types of attacks. We have audited all Web site blogs we host and Pingbacks have been turned off. Moving forward, all new sites will have Pingbacks disabled. WebSight Design's hosting services are secure and rigorously monitored. We are highly focused on protecting our clients from the monsters roaming the world wide web.